Mart Networks launches Invinsense 6.0, an advanced AI-powered cybersecurity platform designed for Af...
- Crypto Crackdown: Kenya Introduces New Bill to Regulate Digital Assets
- How a U.S. Law Change Could Impact the Global Internet and Online Freedom
- Telkom Kenya Lands KSh 570M Contract for Open RAN Expansion
- Nvidia CEO: The Future of AI Will Require 100x More Computing Power
- The AI Race Heats Up: Breakthrough Innovations from OpenAI, Google, and China’s Rising Tech Titans
- Google Offers Gemini Code Assist Free to Individual Developers
- Alibaba Unveils Wan 2.1 AI Model to Compete with OpenAI
- Internet Disruptions Hit Nairobi Amid Escalating Feud Between City Hall and Kenya Power
- Epson Appoints New President & CEO to Drive Global Innovation and Growth
- Ethiopian Airlines and Airbus Sign Flight Hour Services Agreement to Boost Fleet Efficiency
Security
Worried about a data breach? Learn the essential steps to protect your personal information, prevent...
Discover how social engineering exploits human psychology to steal sensitive data. Learn about phish...
Discover the most unsettling AI websites that raise serious ethical and privacy concerns. From deepf...
A new KnowBe4 AFRICA survey reveals 58% of Africans fear financial losses from cybercrime, nearly do...
A recent Kaspersky survey reveals that over half of children in the META region are exposed to viole...
Keep your Smart TV secure from cyber threats with essential safety tips. Learn how to update softwar...
The latest Sophos report highlights growing concerns among 89% of IT leaders regarding potential fla...
The "Nigerian" scam has evolved into sophisticated forms like romance schemes, business investment f...
Kaspersky has uncovered a novel malware operation called SparkCat that uses advanced OCR technology ...
Kenya bolsters its defense with six Bayraktar TB2 drones from Turkey. Learn how these advanced UCAVs...
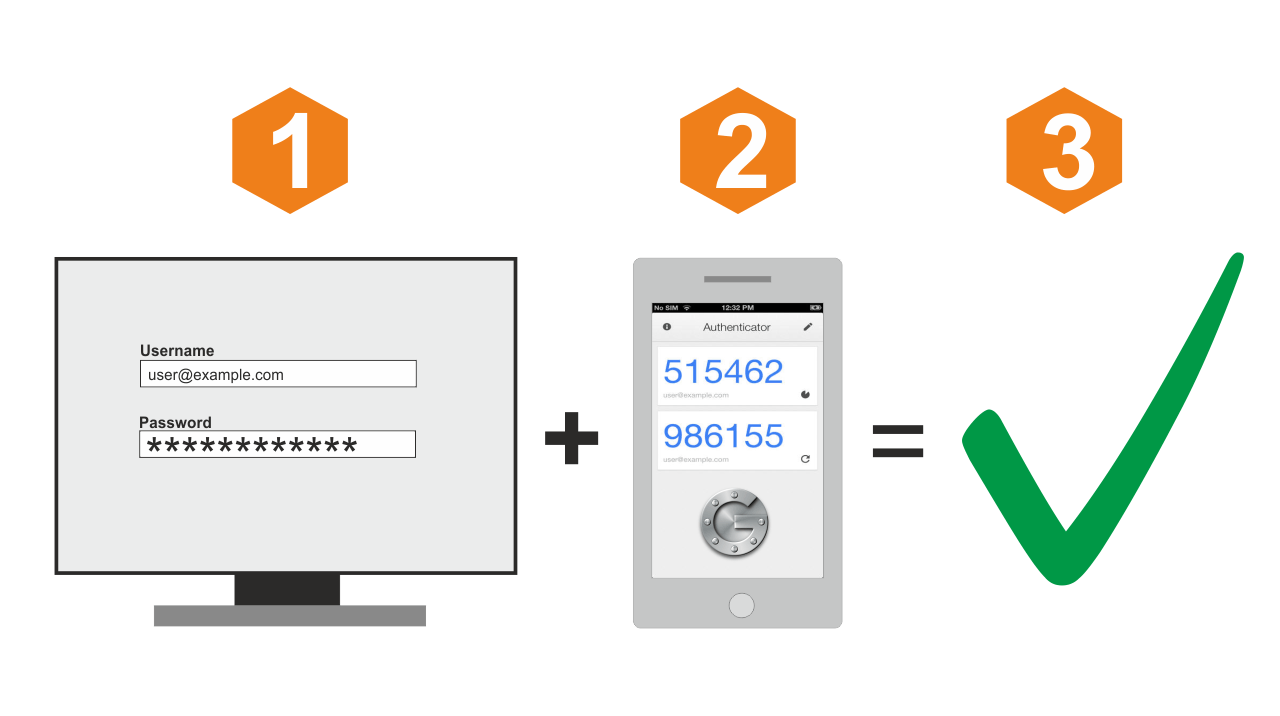
Learn how Gmail two-factor authentication (2FA) boosts security by requiring more than just your pas...
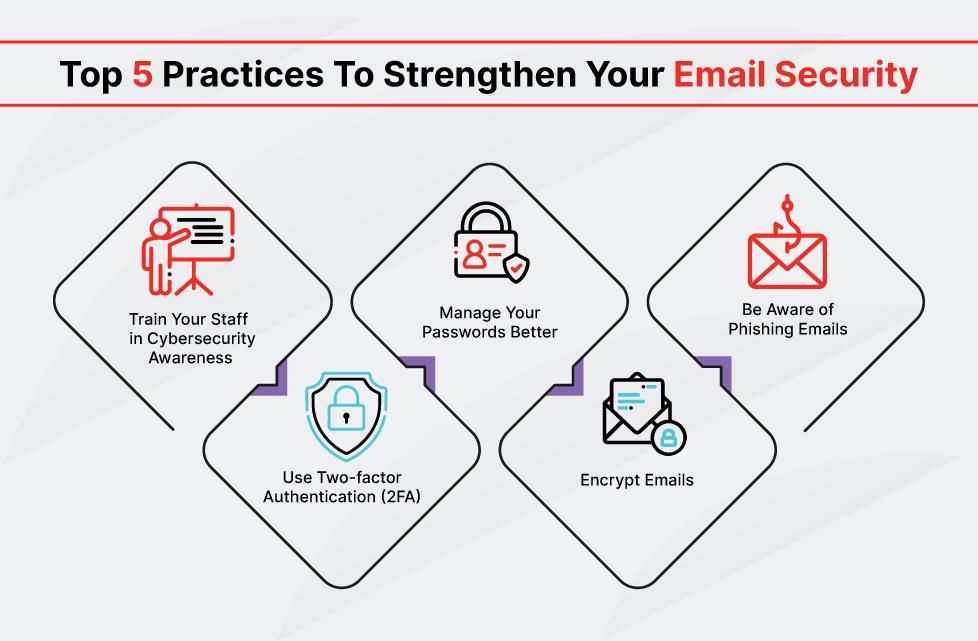
Protect your organization from email threats like phishing, spoofing, and malware with top email sec...
Discover common cybersecurity threats like URL interpretation, DNS spoofing, session hijacking, and ...
MONITORAPP Inc. announces its strategic expansion into the Middle East and Africa through new partne...
Kaspersky introduces a new AI-focused module within its Automated Security Awareness Platform (ASAP)...
Explore the booming data center market expected to exceed $430 billion by 2028, driven by AI technol...
Discover insights from the latest Kaspersky report highlighting a 5% increase in cyber infections ta...
Discover how the Ghana Cybersecurity Authority is addressing a rise in cyberbullying cases linked to...
Stay informed about the WARMCOOKIE Windows backdoor targeting job seekers through phishing emails. L...