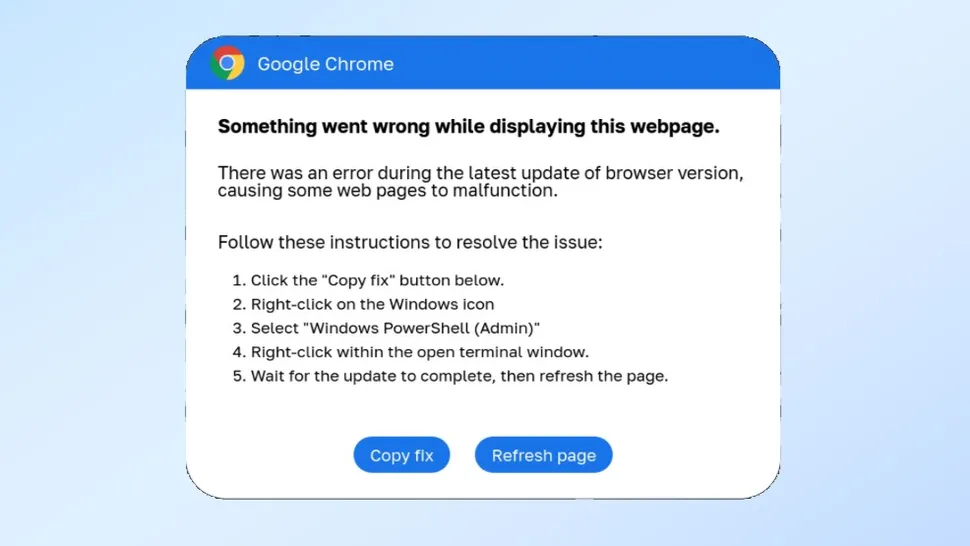
Beware of a sophisticated malware campaign using fake Google Chrome and Microsoft Word errors to tri...
- Crypto Crackdown: Kenya Introduces New Bill to Regulate Digital Assets
- How a U.S. Law Change Could Impact the Global Internet and Online Freedom
- Telkom Kenya Lands KSh 570M Contract for Open RAN Expansion
- Nvidia CEO: The Future of AI Will Require 100x More Computing Power
- The AI Race Heats Up: Breakthrough Innovations from OpenAI, Google, and China’s Rising Tech Titans
- Google Offers Gemini Code Assist Free to Individual Developers
- Alibaba Unveils Wan 2.1 AI Model to Compete with OpenAI
- Internet Disruptions Hit Nairobi Amid Escalating Feud Between City Hall and Kenya Power
- Epson Appoints New President & CEO to Drive Global Innovation and Growth
- Ethiopian Airlines and Airbus Sign Flight Hour Services Agreement to Boost Fleet Efficiency
Security
Check Point and Microsoft have teamed up to enhance Infinity AI Copilot with Microsoft Azure OpenAI ...
Explore the mysteries behind ad recommendations on platforms like Facebook, Instagram, and Kenyan ne...
Security experts warn of active exploitation of high-risk vulnerabilities in ConnectWise's ScreenCon...
The FTC bans Avast from selling users' web browsing data to advertisers, settling charges with a $16...
Explore the lucrative world of ransomware in 2023. Discover how hackers doubled their known payments...
Tech giants, including Microsoft, Meta, Google, Amazon, and IBM, pledge to combat election-related d...
TheTruthSpy, stalkerware, Android devices, security flaw, hacking groups, SiegedSec, ByteMeCrew, dat...
Bugcrowd, a leading cybersecurity platform, secures $102 million in an equity round led by General C...
As of 2023, internet restrictions persist globally, with Africa experiencing 17 cases, notably in Se...
WhatsApp introduces a new feature enhancing user privacy and security. Users can now block spam mess...
Safaricom implements a groundbreaking telecom directive, ceasing unregistered mobile money transacti...
“Unleashing Titans: The Dance of AI in Cybersecurity and Cybercrime’s Dark Symphony̶...
“Cracking the Code: The Ransomware Riddle and Tips for Outsmarting Cyber Crooks” As the ...
In the dynamic and ever-evolving landscape of the digital realm, children are stepping into the onli...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investiga...
“Ukrainian Wunderkind’s Crypto Crime Spree Unveiled: 29-Year-Old Whizkid Nabs $2 Million...
Malware is exploiting an undocumented Google OAuth endpoint called MultiLogin, allowing attackers to...
Google has agreed to settle a lawsuit filed in June 2020, accusing the company of misleading users a...
The Iranian nation-state actor, MuddyWater, has been using a new command-and-control (C2) framework ...